A Deep Dive into App Authentication: Techniques and Best Practices
The importance of protecting user data has never been higher as the world becomes more digital. In this regard, authentication methods in mobile and web apps are the most reliable ways to keep user data safe.
App authentication methods ensure that only authorized users can access an app’s features and functions. Developers can choose from a wide range of authentication methods, each with its strengths and weaknesses. So, what are the significant types of authentication methods? No worries.
This article will explore the different authentication methods developers can use to ensure safe user data. So developers and users alike, this guide will help you make informed app security decisions. Read on to learn more.
What is Authentication?
Authentication is verifying a user’s or device’s identity attempting to access a system or application. It’s a fundamental security measure that ensures only the right people can access sensitive information.
Mobile and web applications typically require users to enter their login credentials, such as a username and password. The app then sends these credentials to a server for verification. The app’s features and functions are accessible if the credentials match what’s on record.
Authentication can take many forms, from simple username and password combinations to multifactor authentication. The authentication method depends on the app’s security level and the sensitive data the user wants to access.
Types of Major Authentication Methods
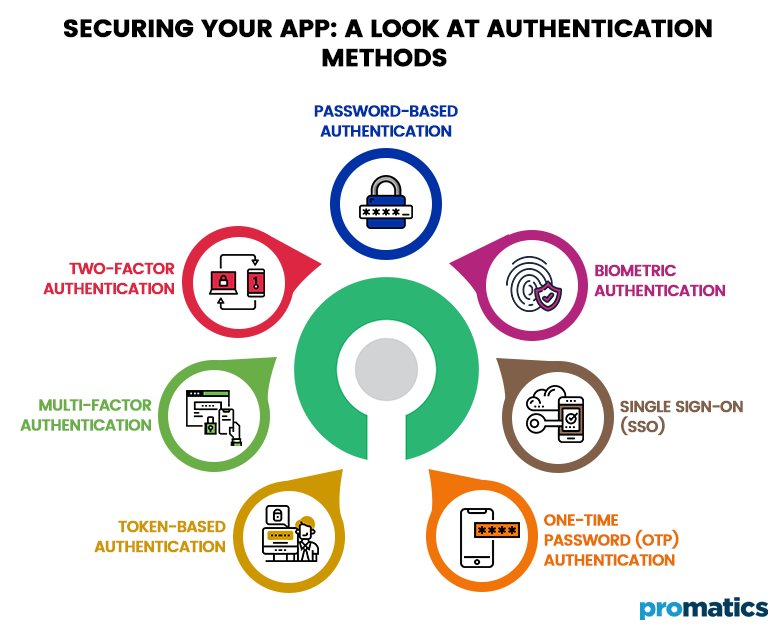
Mobile and web apps can verify a user’s identity using several authentication methods. Here are some of the major types of authentication methods:
Password-Based Authentication
The most common method of authentication is passwords. An individual’s password may consist of letters, numbers, or special characters. You should create strong passwords that incorporate different options to ensure strong security.
Despite this, passwords are often vulnerable to phishing attacks and poor security habits. It is estimated that the average person has over 25 online accounts, but only 54% use unique passwords.
Moreover, it can be challenging to remember a large number of passwords. Therefore, people tend to use simple passwords that are easy to remember over secure ones.
Ultimately, more than passwords is needed are to protect your online info because they have numerous weaknesses. Hackers can quickly get user credentials by systematically testing all possible combinations. In addition, typing passwords on a small smartphone screen is a frustrating experience.
The most common password-based authentication methods are:
- Static passwords: Static passwords require the users to create a fixed password, which they must enter to access the app. It is the most common type of password-based authentication.
- Dynamic passwords: Dynamic passwords are generated passwords that are valid for a limited time.
Two-factor authentication (2FA)
It adds an extra layer of security to password-based authentication by requiring the user to enter a one-time code. For example If someone guesses your password, it is unlikely they would also obtain the one-time code given to your device. While this makes it harder for hackers to gain unauthorized access, users may find it more hassle.
The most common two-factor authentication methods are:
- SMS-based authentication: Requires users to enter a one-time code to gain access, which they receive via SMS. It is the most commonly used type of 2FA.
- Email-based authentication: Email-based authentication lets you gain access by entering a one-time code you get via email.
- App-based authentication: App-based authentication generates one-time codes using a mobile app. Users have to enter the code generated by the app to gain access.
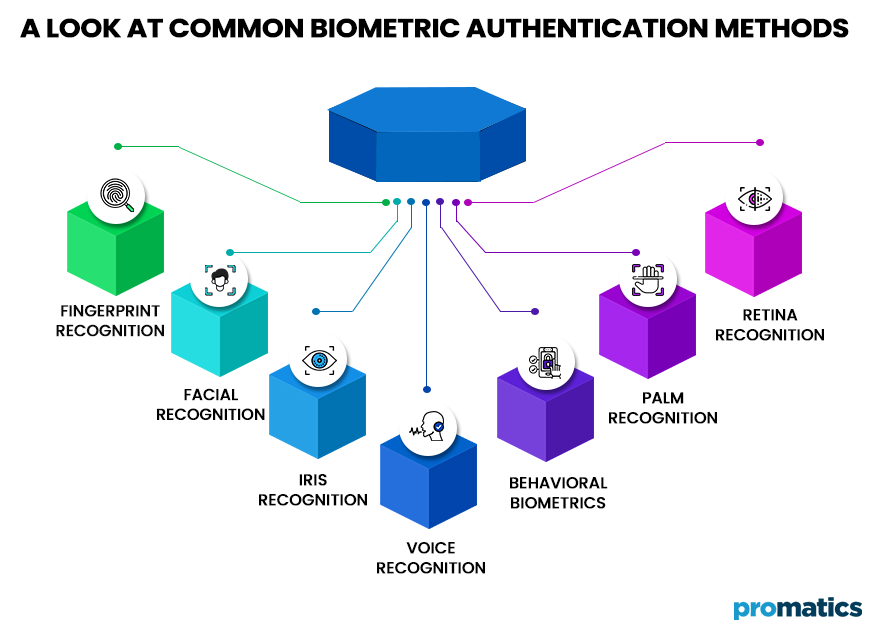
Biometric Authentication
Biometric authentication uses unique physical or behavioral traits to verify an individual’s identity. Increasingly, it is used in many fields to reduce the risk of identity theft and fraud, including finance, healthcare, and security.
There are many different biometric authentication methods, each with strengths and weaknesses. The following are some of the most common biometric authentication methods:
- Fingerprint Recognition: It’s the most common and widely used biometric authentication method. It identifies individuals based on their unique fingerprint patterns. Using fingerprints, the system confirms the user’s identity by comparing the data with a database of prints.
- Facial Recognition: This method authenticates the user by capturing the user’s facial features and comparing them to a database of facial images.
- Iris Recognition: This method uses a camera to capture an image of the user’s iris. Afterward, the image is compared with iris images in a database.
- Voice Recognition: The method captures the user’s voice and compares it to a database of voice prints to authenticate the user.
- Behavioral Biometrics: Using behavioral characteristics like typing speed, mouse movements, and navigation patterns, this method authenticates the user.
- Palm Recognition: It captures a user’s palm print, compared to a database of stored palm prints to authenticate them.
- Retina Recognition: It uses a camera to take a picture of your retina, which is then compared to a database of retina pictures.
Multi-Factor Authentication (MFA)
The Multi-Factor Authentication (MFA) technique requires two or more user identification methods. Examples are smartphone codes, Captcha puzzles, fingerprints, voice biometrics, and facial recognition.
MFA authentication methods and technologies make users feel more secure since they add more layers of protection. Even though MFA may be a good barrier against most account hacks, it has its drawbacks. If someone misplaces their SIM card or phone, they can’t generate an authentication code.
Single Sign-On (SSO)
The single sign-on (SSO) method allows users to access multiple applications and systems through a single login. While maintaining a high level of security, this approach streamlines the authentication process and improves the user experience.
SSO allows users to authenticate once, then gain access to all authorized applications and systems without repeatedly entering their login credentials. It is commonly used in enterprise environments where users need to access multiple applications and systems.
SSO typically uses one of the following protocols:
- Security Assertion Markup Language (SAML): The SAML Protocol exchanges authentication and authorization data between parties, like identity providers and service providers.
- OpenID Connect (OIDC): OIDC is an authentication protocol that provides identity verification and security features for web and mobile applications.
- OAuth: OAuth is a protocol that lets users grant limited access to resources from one site to another without sharing their login info.
Token-Based Authentication
Token-based authentication uses a token or a digital signature to authenticate users and grant access to an application. It provides enhanced security and eliminates the need for passwords in web apps and APIs.
Token-based authentication lets users provide their login credentials, which are then verified by the server. The server sends a token back to the client after successful authentication. The client then includes this token in all subsequent requests to the server to gain access to protected resources. Whenever a request comes in, the server checks the token and grants access if it’s valid.
One-Time Password (OTP) Authentication
It involves sending the user a one-time password, which they then enter into the app to verify their identity. This method is commonly used by apps such as WhatsApp and can be more secure than password-based authentication.
Best User Experience Practices for App User Authentication
Here are some best user experience practices for app user authentication:
Streamline the Authentication Process
Simplicity is key because complicated authentication can cause frustration and user abandonment. For example, single sign-on (SSO) simplifies the process by letting users use their existing credentials to access multiple apps. Another option is to use a password manager that generates complex passwords and automatically logs users in.
Use Clear and Concise Language
Using clear and concise language is important to ensure users understand the authentication process. You should refrain from using technical jargon or complex terminology that users might need help understanding. Help users understand what they have to do during authentication by providing simple instructions.
Providing Feedback
Providing feedback to users as they complete each step of the authentication process keeps them on track and reduces anxiety. For example, a progress bar can be used to show users how far they have progressed in the authentication process. Also, a confirmation message after each step can help users feel on the right track.
Keep Visual Cues in Mind
Visual cues such as icons or graphics can assist users in completing the authentication process. By doing so, users can find the process more intuitive and less intimidating. For example, a lock icon indicating that a user is entering a secure area can reassure them that their information is safe.
Offer Multiple Authentication Options
Offering multiple authentication options can cater to different user preferences. Some people want biometric authentication, like fingerprint scanning, while others want an OTP. With multiple options, users can choose what works best for them.
Implement Error Handling
You should implement error handling to reduce user frustration and improve the user experience. If a user enters the wrong login credentials, the system should give them clear feedback on what went wrong. In addition, the system should prevent users from being locked out after too many failed logins.
Make Password Reset Easy for Users
You’ll prevent users from getting frustrated by providing an easy and straightforward way to reset passwords. This can include options such as sending a password reset email or using a security question to reset the password.
Test the Authentication Process
It’s important to test the authentication process to identify potential problems thoroughly. Tests can help you get user feedback and make changes based on that. Analytic tools can also provide valuable insights into how users interact with authentication processes and where improvements can be made.
Optimize for Accessibility
Provide images with alternative text or high-contrast colors for visually impaired users to make the authentication process accessible.
The Biggest Authentication Trends of the Future
Here are some trends to watch in the authentication process in the future.
Implementing AI for Predictive Security
AI could revolutionize authentication by providing predictive security measures in the future. With AI, authentication systems can detect suspicious behavior and prevent security threats before they become a problem. Artificial intelligence can analyze millions of data and detect unusual patterns in user behavior using machine learning.
Eventually, AI might make authentication faster and more seamless for users by automating it. An AI-powered authentication system can learn from user behavior and adjust authentication accordingly, providing a more personalized and efficient experience.
Furthermore, AI can improve biometric authentication by identifying potential spoofing attempts and improving accuracy.
Moving Beyond Password Policies
Traditionally, organizations have relied on password policies to enforce safe password practices. However, as passwords get more complex, they’re harder to remember. Thus users write them down or re-use them across multiple accounts, compromising security.
Thus, password policies are being replaced by alternative authentication methods, which are more secure and easier to use. These include biometrics, tokens, and risk-based authentication, which can detect and prevent fraudulent activities by using machine learning and behavioral analysis.
Adoption of Passwordless Authentication
The passwordless trend eliminates passwords and replaces them with more secure and convenient methods, like biometrics and tokens. This approach offers better security and a better user experience. Users no longer have to remember complex passwords or worry about forgetting them.
Instead, they can use a more intuitive and natural authentication method, like their fingerprints. We can expect more organizations to adopt biometrics and token-based authentication methods in the coming years.
Removing User Password Control
For years, users have had full control over their passwords, including creating and managing them. However, this approach can lead to weak passwords, password reuse, and other security problems. As a result, organizations are taking away user password control and switching to passwordless or other more secure authentication methods.
Additionally, removing password control makes the user experience more convenient. Users no longer have to remember complex passwords or worry about forgetting them. Alternatively, they can use a more natural and intuitive authentication method, such as fingerprint or face recognition.
The Takeaway
In today’s digital age, where identity theft and data breaches are on the rise, protecting user data is paramount. So, the right authentication method can make a huge difference in your app’s adoption and security.
There’s a variety of authentication methods available for app developers, from traditional usernames and passwords to modern biometrics. However, different factors like security, user experience, and regulatory compliance determine the best authentication method.
Hopefully, you will find this guide helpful in making an informed choice regarding authentication methods.
Still have your concerns?
Your concerns are legit, and we know how to deal with them. Hook us up for a discussion, no strings attached, and we will show how we can add value to your operations!