How to take care of security while developing mobile apps?
In today’s competitive world, many people and businesses are using business technology increasing the chances of exposure to security and identity threats. It is estimated that more than 52% of people across the globe spend at least 2 hours on mobile apps.
Thousands of new apps hit the market every week, which give hackers an opportunity to tap into these apps and phish the confidential information of user orimplant a malware. App developers must be vigilant about the security of users. It is better to catch the security flaws at the time of app development process, rather than incorporating them at the time of launch or after launching the app.
Mobile apps available through reputed app stores such as Google’s Play Store and Apple’s App Store are the dominant form of delivering value to users across the globe.
But, are these mobile apps really secured?
Well, recent research from Arxan (State of Security in App Economy) determined that 100% of the top paid apps on Google Android platform are hacked – and more than 56% of top paid apps on Apple are hacked.
The fact is that more than 80% of people use the same phone for personal and professional use. This trend will impact the user experience, reducing the ability of IT department to give secured access to data on enterprise system.
So, how to take care of security while developing a mobile app? In this post, I will guide you through a few methods that help you take care of security.
1. Building a secure application
Mobile malware often attacks the design and code of mobile apps. It is estimated the malicious code infects more than 11.6 million mobile devices at a time and the number of expected to increase by twentyfold by 2023. Attackers can obtain a copy of application and reverse engineer it —- and repackage into “rogue apps” that contain malicious code. These apps are posted on third-party stores to trick unsuspecting users to install them.
Mobile app developers should look for tools that detect and close security vulnerabilities — and harden their apps against reverse engineering and tampering. Enterprise apps represent a threat, as they may not undergo appropriate hardening process.
Network and data security are important parts of security picture. However, the security has to start with the app itself — as vulnerabilities caused by developer error may be targeted specifically by the hacker. Always protect the app with encryption and stick with well supported algorithms.
2. Developers should secure the device
The security of a mobile app depends on the underlying device’s security as well. Rooted devices can represent execution risk that may be allowed for certain enterprise apps, but not other apps. Companies should always look for ways to gauge the security of the device. It is highly recommended to restrict the devices from accessing enterprise data. Jailbreaking the device breaks the underlying security model, and it is must to cope up with these threats.
Excessive use of permissions to mobile apps can provide rogue applications and malware an easy access to basic services, facilitating fraudulent activities. Enterprises should consider updated intelligence sources to track tidal wave of applications and their associated risk – as they enter the mobile store every day. This data can be used to enable or disable application capabilities based on the risk profile of the device
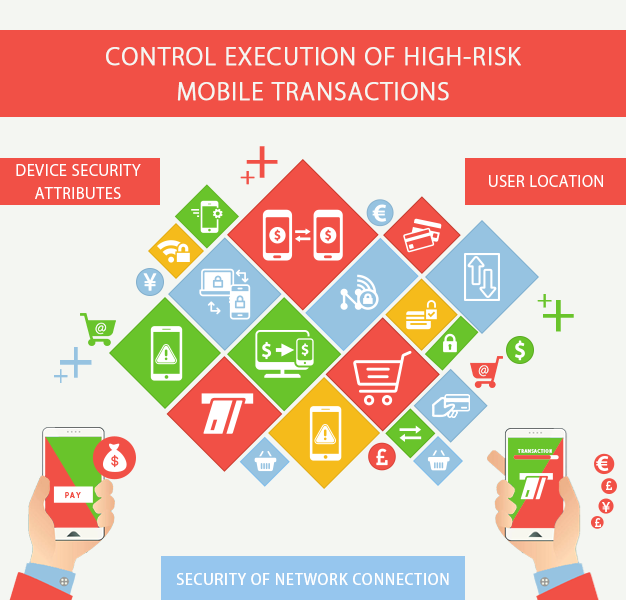
3. Control execution of high-risk mobile transactions
All the high-risk mobile transactions should be secured, based on which companies should adapt an approach of risk-aware transaction execution that restricts client-side functionality. Some of the risk factors include – device security attributes, user location and security of network connection. When the client transactions are allowed, enterprise applications can leverage an enterprise mobile risk engine to correlate risk factors such as – IP velocity.
This approach extends the enterprise ability to detect and respond to complex attacks that can span multiple interaction channels.
The risk tolerance for transactions may vary from one domain to the other. For instance – HR related content may have low risk compared to finance management.
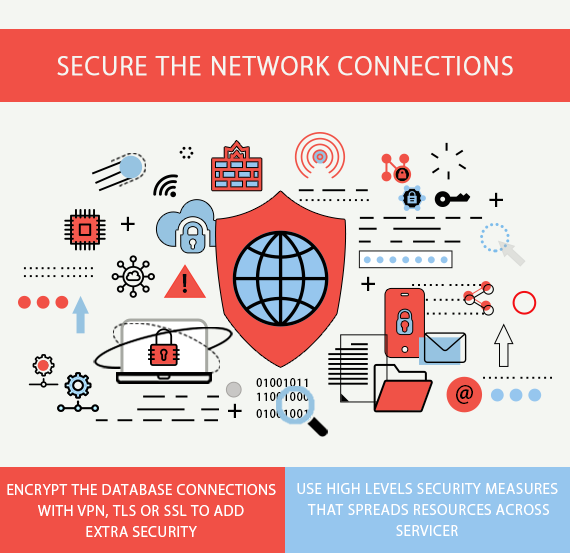
4. Secure the network connections
The servers of apps API should have strong security measures in place to protect data and prevent unauthorized access. APIs should be verified to prevent eavesdropping on confidential information passing from the client back to app server’s database.
You should consult a network security specialist to conduct vulnerability assessments of your network and ensure the right data is protected in right way. Encrypt the database connections with VPN, TLS or SSL to add extra security.
Use high levels security measures that spreads resources across servicer so that they are not in one place.
5. Test the app again and again
Testing app code is one of the important steps in an app development process. Today, apps are being produced rapidly — as a result of which the most important process falls to the wayside to speed up time to market. When testing the functionality of app, experts advise developers to test it for security.
Penetration testing entails probing a network or system for weakness. It is better to test the app thoroughly for authentication, data security, identify fraud and theft etc, in case the device is stolen. Make the devices risk-aware so that any attempt to make certain transactions is blocked from doing so. Apps can be coded to detect as well as blockcertain transactions from rooted devices.
Unit testing is another test that developers can perform to test smallest parts of application on their own. The process of combining smaller units and testing them in multiple ways is called integration testing. Developers can use it to test the “outside” aspects of an app such as – hardware, interfaces, databases etc.
6. Secure the data stored in the app
Insufficient data storage makes it easy for hackers to access personal information stored in the app. You can take a few steps to secure data stored on mobile devices. The first and foremost thing is to transmit and display data without storing it in app’s memory.
If the data needs to be stored, we recommend storing the data in RAM so that only bits and pieces of information can be accessed at a time. When the application closes, the data also closes.
Besides this, you can add multiple layers of encryption such as – SQLCipher. Remember that there are multiple layers of data protection on an iOS platform. You can even take help of third-party cryptography so that only authorized readers can process the data.
Conclusion
Securing the mobile app is all about finding a balance between usability and mitigating risk. An appropriate mobile security framework will enable enterprises to reap the benefits of productivity and at the same time protect all the confidential information. An experienced mobile app developer can help you respond quickly to the threats and bugs.
The above six methods in the appemphasize the importance of addressing security throughout the development process. Though these methods of security may seem challenging, it is actually easy to think about the apps in parts. Have a look at each of the above method and examine the app for related security issues.